on
CoSNARKs in Action: Private Proof Delegation
The ZK stack has finally matured to a point where zero-knowledge applications are moving from theory to reality. Today, we have ZK apps like ZKP2P for web proofs, ZK email for secure email verification, and Rarimo for identity verification, enabling users to prove statements without revealing their private data. These early applications give us a taste of a privacy-centered, verifiable web. But as these apps grow, so do the challenges: many still depend on client-side proving, which can be limiting due to resource constraints.
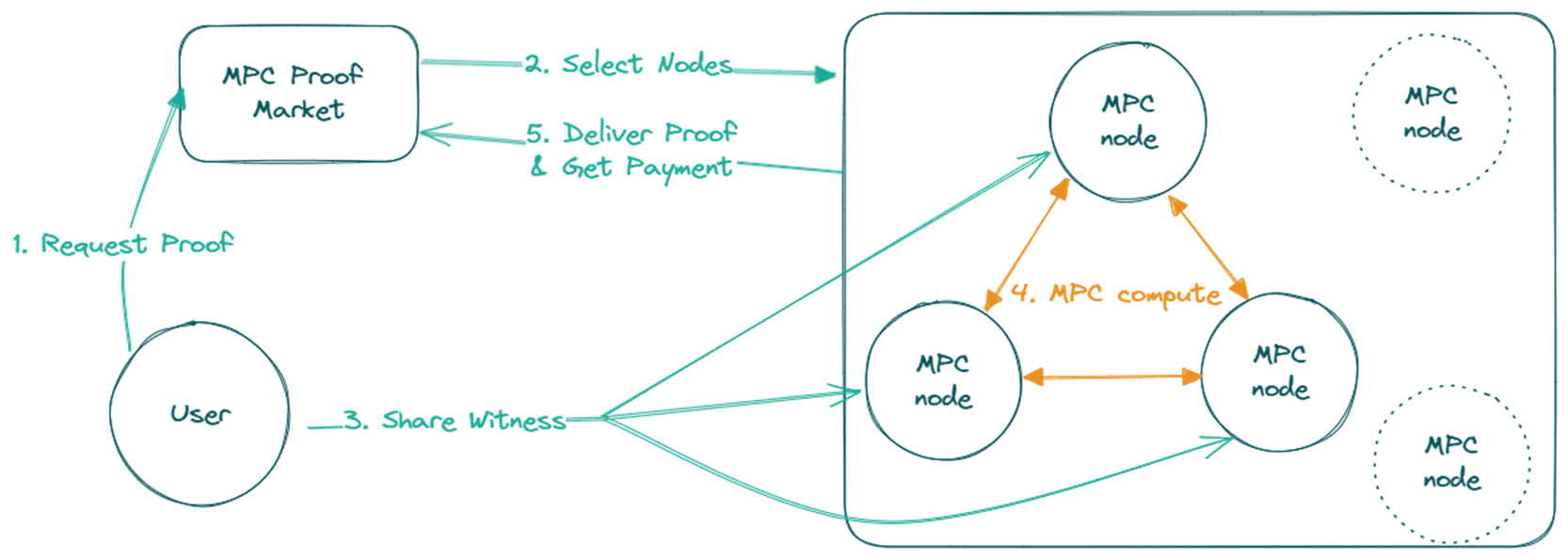
Proof markets are offering a way to outsource proof generation to powerful external servers. But here’s the rub—outsourcing proofs means sending sensitive data to third parties, creating a new privacy gap. This raises an important question: can we delegate proof generation without risking our privacy?
The answer is collaborative SNARKs. In this post, we’ll explore how coSNARKs enable private proof delegation, and the impact this can have on ZK applications.
From Theory to Practice: Why ZK Applications Need More Power
Imagine this: you're using your favorite ZK app, whether it’s for secure email, verifying your identity, or something entirely new. You hit “generate proof” and wait… while your heart beats 60-100 times, a hummingbird flaps its wings thousands of times, and NASA receives a fresh stream of data from Mars rovers. During that pause, you might wonder, “Why can’t a more powerful server handle this for me?”
Offloading proof generation to faster, external hardware could make the user experience far more efficient. But there’s a problem: privacy. In most ZK applications, the data being proven is sensitive—personal identity details, financial history, or transaction data. Passing that data to an outside server for faster proof generation contradicts the privacy-first principles ZK technology stands for.
How CoSNARKs Enable Secure, Scalable Proofs
CoSNARKs use Multiparty Computation (MPC) to enable private proof delegation without sacrificing security. Rather than sending data to a single third party, coSNARKs distribute the computation across multiple parties. Here’s the crucial bit: each party only works with an encrypted share of the data, meaning no one ever sees the entire picture. This setup not only preserves privacy but also lets users access the speed and power of decentralized proof markets. Each party involved computes on encrypted fragments of the data, ensuring that no single entity ever has the full view.
The result is a leap forward for ZK applications that need both speed and privacy. Builders can securely outsource proof generation, opening up possibilities for a wide array of applications. Imagine DeFi lending platforms that can quickly verify creditworthiness without exposing transaction histories, identity verification systems that keep personal details confidential, and private voting mechanisms in DAOs where votes are kept private while results are verifiable.
Real-World Scenarios: Where CoSNARKs Make a Difference
CoSNARKs are useful when both privacy and heavy computation are needed—situations where a user’s device just can’t handle the load. Here are some examples of where coSNARKs make all the difference:
- Identity Verification and Connection Discovery: Existing ZK apps around web proofs, identity verification, and connection discovery allow users to confirm statements or connections without disclosing sensitive data. But to scale these functionalities without slowing down the user experience, coSNARKs could enable the heavy lifting to happen off-device, securely delegating proof generation to trusted nodes while keeping private information fully protected.
- DeFi Lending: In decentralized lending, proving creditworthiness might require analyzing large sets of financial data—far beyond what mobile devices can handle. With coSNARKs, users can delegate this proof generation to an MPC environment without exposing sensitive data, allowing coSNARKs to collaboratively produce a privacy-preserving proof.
- Identity Verification for Complex Profiles: Verifying identity through multiple factors—such as multi-factor credentials or biometrics—can quickly exceed typical device capacity. With coSNARKs, identity apps can distribute the computational load while keeping personal data secure and scalable.
- Proof Markets for Resource-Intensive Applications: Some applications, like verifying machine learning models or conducting large-scale financial audits, require intense computation. With coSNARK-enabled proof markets, users can outsource these proofs while keeping private data hidden. If you’re curious, check out Daniel’s talk at ZK Summit 11 to learn more.
Balancing Privacy and Performance: A Practical Approach
With coSNARKs, there are two main tasks involved in generating a proof: witness extension and proof generation. Witness extension converts the witness into the format needed to generate proofs in MPC, while the proof itself is the final output that allows to verify a statement without revealing the underlying witness data. When it comes to delegating computation, you can choose to privately outsource either one or both of these steps to an MPC network.
Here's why this distinction matters: proof generation is far more resource-intensive than witness extension. Our research shows that proof generation needs about 5 times more memory than witness generation. For example, a proof might require 8GB of RAM, which is beyond what most smartphones can handle, while witness generation only needs about 2GB, making it possible on higher-end mobile devices.
For the most efficient setup, you could generate the witness locally on your device, secret share to the MPC network, and delegate the proof generation, which saves both memory and processing power. Outsourcing proof generation also removes the need to bundle heavy proving libraries in the app itself, which keeps apps lightweight and lowers the need for frequent updates to maintain security. Proofs generated on external servers are typically fast—often completed in under a second—making this a practical solution for real-time applications.
For those who want full flexibility, coSNARKs support private delegation of both the witness and proof generation to the MPC network. This means you can keep the entire computation private while offloading all the heavy lifting to a secure, distributed network, so your device isn’t strained, and your privacy is fully preserved.
Open Challenges in Proof Delegation
While coSNARKs bring significant benefits to privacy and scalability in proof delegation, they're not without their own set of challenges.
One key issue lies in multiparty performance bottlenecks. Coordinating multiple parties to work on distributed proof generation can create computational overhead, as each party's tasks must be synchronized for the proof to be valid. Improving the speed and efficiency of these multiparty processes is an active area of research, with promising first benchmarks showing gains but leaving room for optimization. Achieving low-latency collaboration without sacrificing performance will be crucial to mainstream adoption.
Additionally, network communication remains a significant hurdle. Multparty proof generation requires data to be shared across different servers, and network latency can limit performance. Delays in data exchange between servers impact the overall efficiency of the system, particularly in real-time applications. We have already made some communication optimizations, but still developing faster communication protocols is essential to enhance the performance of coSNARKs, especially as applications scale and user expectations for speed increase.
Looking ahead, overcoming these challenges will be key to enabling coSNARKs to meet the demands of large-scale, privacy-centric applications. Each improvement in multiparty performance and network efficiency brings us closer to a seamless, privacy-preserving experience in proof delegation.
What's Next?
Curious to explore the future of private proof delegation yourself? Dive into our coCircom and coNoir tooling, and join our community as we push the boundaries of privacy-preserving tech. Check out our tools here, join the developer discussion on Discord and if you’d like to follow the updates, register for our upcoming newsletter!