on
The Encryption Trifecta
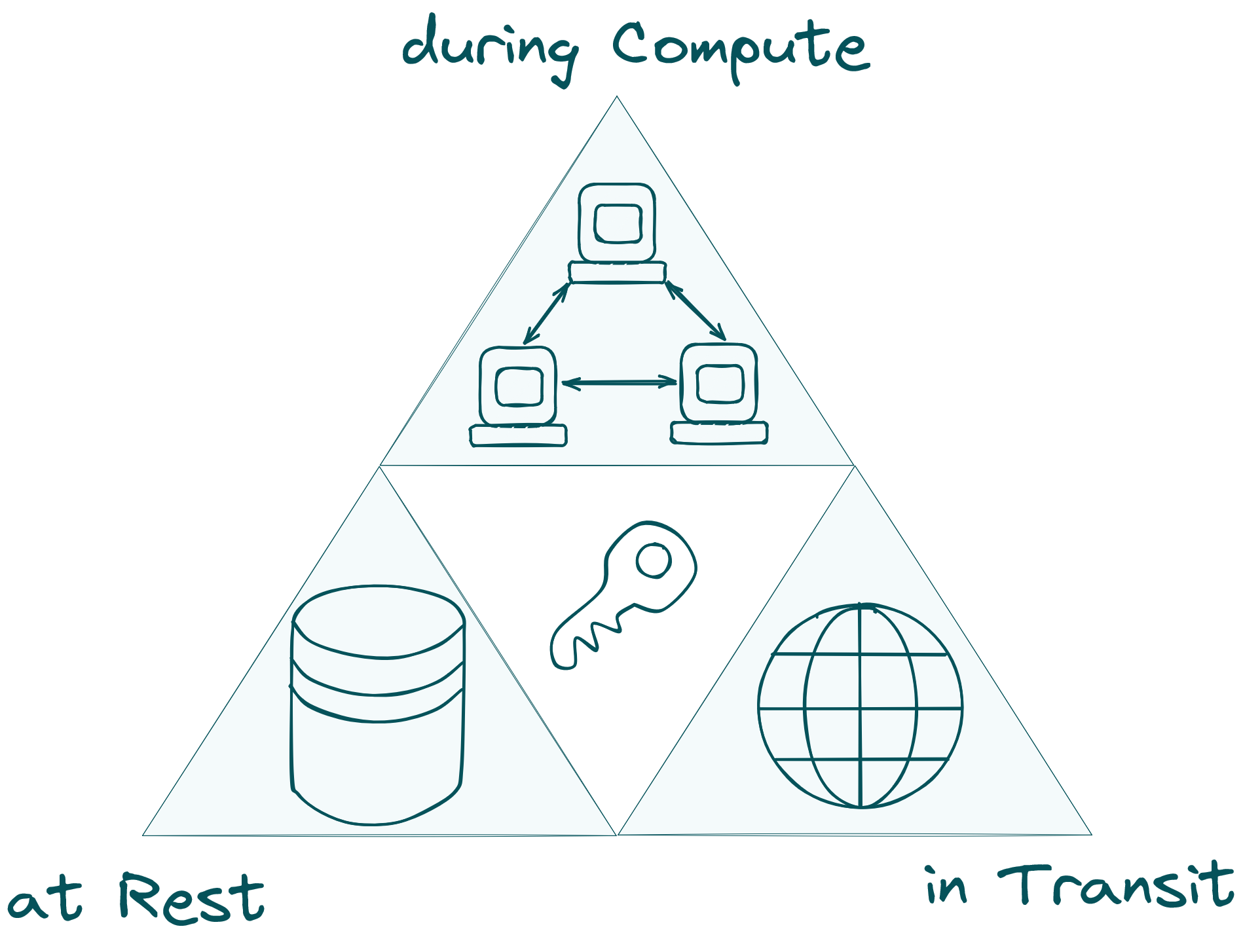
Imagine a world where your data is not only encrypted at rest (AES) and in transit (TLS) but also during computation. Welcome to the future of blockchain technology with Compute Layer Security (CLS). In this blog post, we dive into the groundbreaking vision of making encrypted computation the default, transforming blockchains into decentralized systems with provable privacy.
The Missing Infrastructure for Encrypted Compute
The first real-world encrypted computing use case dates back to 2008, involving an auction for sugar beets. However, most auctions in the blockchain context still rely on intermediaries instead of leveraging cryptographic guarantees. So, if the technology is already out there for quite some time, you might ask: Why isn’t encrypted computing more widespread? While people might not prioritize privacy and decentralization for their own sake, they certainly value fair pricing, control over their digital identities, and ownership of their digital connections and assets.
The primary reason most projects are still experimenting, with only a few deploying encrypted compute on a large scale, is the lack of robust infrastructure. Although there are libraries and tools available, they come with significant overhead and steep learning curves. We often hear that things will improve and that only a small portion of applications need private computation. We see this differently. In fact, we only see one way forward: blockchain computations must be private by default. Before explaining why, let's clarify what we mean by "default." Encrypted computations should be as easy to integrate as HTTPS and just as widely used. This may seem ambitious, but remember, in the early 2000s, only e-commerce sites used HTTPS. Today, it's nearly universal.
Why Encryption By Default?
Why is it crucial for encrypted computations to be the default? Consider HTTPS again. There was a time when websites used HTTPS only for sensitive data, reasoning that developers could optimize by using unsecured modes for non-sensitive data (mixed content). This approach introduced numerous vulnerabilities. It’s not the developers' fault but rather the flawed idea that one can always predict which data might be misused in a dynamic environment. HTTPS by default liberated developers from these concerns, decoupling security from functionality. The same must be achieved with encrypted computation.
A New Standard: Compute Layer Security (CLS)
To make blockchain computation encrypted by default, we envision the CLS. Think of the CLS as transforming blockchains from decentralized computers into decentralized computers with provable privacy. It completes the encryption trifecta: data at rest (AES), data in transit (TLS), and data in computation (CLS). This trifecta will enable true data privacy and ownership without sacrificing any functionality, allowing computation on private shared states for the first time. This creates a new design space for application developers, including private DeFi (dark pools, intent, MEV protection), data ownership (biometric data handling, verified image editing), gaming (mental poker, multiplayer strategy games), and AI (private ML inference).
As fundamental infrastructure the CLS must have the following properties:
- Open-Source: To ensure widespread adoption, the protocol must be free from any licenses or patents that could restrict its use.
- Community Controlled: The protocol must be managed by the community, not a corporate entity, to encourage third-party development and innovation. Imagine if HTTPS required payment or was owned by a for-profit organization; it would never have become the default.
- Fast: The protocol must operate at such high speeds that users do not notice any performance overhead.
- Reliable: As the guardian of everyone's data, the protocol must be robust and dependable. Building it openly ensures its reliability.
- Interoperable: The protocol must work seamlessly across all platforms and devices, whether it's a smartphone, a refrigerator, a GPU cluster, or a car. The CLS should be ubiquitous.
Encrypted Compute in Action
Imagine a developer working on a multiplayer on-chain game. They could use ZK proofs for each turn, ensuring transparent and secure interactions. However, if their game includes hidden information (fog of war), they typically need a trusted party to manage the players' private states. With an encrypted computation infrastructure as seamless as HTTPS, these challenges are eliminated. This infrastructure guarantees that all computations are private by default, securing the game's data and relieving developers from the role of gatekeeper. This freedom enables them to concentrate on crafting innovative gameplay features.
To the user the CLS is only visible by a small, balanced scale icon in the corner of her blockchain app. This scale symbolizes the active CLS protocol, ensuring her data rights and encryption during computation. When hovered over, it displays, "Encrypted Computation Active: Only essential data shared" providing users confidence in their data's privacy and ownership.
Now, they can use the game and other digital services without fearing data misuse or privacy breaches. It also guarantees fair compensation and protection of intellectual property for creators, even in an era of widespread generative AI. This change enhances user trust and engagement, creating a secure, equitable, and dynamic digital environment where developers can innovate, creators are rewarded, and users are protected.
The Foundation of CLS
Three years after his seminal work on smart contracts in 1996, Nick Szabo envisioned “The God Protocols”, describing them as the most trustworthy third party imaginable—a deity on everyone's side. Advancements in Multi-Party Computation (MPC) protocols at the time proved that such a trustworthy third party could be created. This effectively replaces algorithmic intermediaries with a incorruptible virtual computer. Unfortunately, unlike smart contracts, which materialized with Ethereum, we are still awaiting the realization of “The God Protocols” (or CLS).
Powering CLS with MPC-VMs
At TACEO, we are fully committed to building an efficient MPC-VM to power the CLS. The MPC-VM is designed to operate using multiple cryptographic techniques and various protocol implementations. Two core techniques at the heart of the MPC-VM are secret sharing and collaborative SNARKs (co-SNARKs).
- Secret Sharing: This is the most popular MPC technique. Similar to ZK, the evaluated function is usually represented as an arithmetic circuit. The inputs are secret-shared among the parties. Every party evaluates the circuit locally on their shares and communicates with the other participants when necessary. After the parties finish their computation, they reconstruct the result of the function without ever telling anyone the secret inputs. In practice, the parties computing the function are not necessarily the same parties that provided the inputs.
- co-SNARKs: Co-SNARKs are a very new line of work, emerging in 2022, that combines the best of MPC and zkSNARKs. They enable multiple parties to jointly create a proof of the correctness of a computation while keeping their individual inputs private. Each party contributes to a distributed protocol that generates a single zkSNARK proof, attesting to the correctness of their combined computation without revealing any individual inputs. The resulting proof is succinct and can be verified efficiently by anyone, ensuring the integrity of the computation without exposing any sensitive data.
Connecting everything
The CLS protocol, combined with MPC-VMs, will form a vast, modular blockchain network. This network will feature heterogeneous computational nodes, ranging from general-purpose servers to dedicated GPU clusters for private AI and specialized ZK hardware. It will be versatile enough to be utilized by all L1/L2 solutions and decentralized applications. Complementing global computation (public state) and independent computation (single private state), this network will efficiently handle mediated computation (private shared state). Smartphones, refrigerators, and other devices will participate as clients, performing computations related to their own requests.
Join Us in Building the Future
Building the CLS is an enormous undertaking and one of the fundamental tasks in the new computing paradigm introduced by blockchains. To achieve this vision, we need the help of the community. Whether you are a researcher, developer, or builder in the areas of MPC, ZK, compilers, or networking, or a privacy enthusiast passionate about data security, we invite you to join us. If you are a tinkerer drawn to encrypted computation because you want to be at the forefront of innovation, or an app developer eager to explore the new design space of encrypted compute for your application, we need your expertise and enthusiasm. Together, we can build a secure, private, and decentralized backbone for the next era of computing and the internet.
Find more details in docs and follow us on X to get the latest updates.